 I recently completed a dehacking project for one of my customer WordPress sites. The site had been the target of multiple brute force attacks and one of the user passwords was compromised by a bot. Once the hacker had access, files were created on the server that corrupted the website and spam links were injected on many posts and pages. Without going into too much detail, dehacking the site was a major pain in the rear, a multi-hour affair.
I recently completed a dehacking project for one of my customer WordPress sites. The site had been the target of multiple brute force attacks and one of the user passwords was compromised by a bot. Once the hacker had access, files were created on the server that corrupted the website and spam links were injected on many posts and pages. Without going into too much detail, dehacking the site was a major pain in the rear, a multi-hour affair.
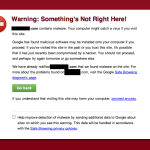
The worse part of the situation was Google picked up on the site hack and displayed a HUGE red “This site has been hacked” message upon entry to the site and also displayed a message in the SERPs. It took several weeks to get the messages removed. In the meantime, site traffic dropped down to nothing. For all the intents and purposes, the website was shutdown.
Dehacking Resources
Here is the Hacking FAQ I reviewed to help with dehacking my customer site. After spending many hours trying to dehack the site on a page by page basis and combing through .php files on the server, I realized it would be more effective to completely blow away the site, stand up a new WordPress instance, and restore the site from a backup. Which is what I ended up doing. It’s the most effective way to ensure your site has been cleansed of the malicious code. I reviewed this guide also before doing that.
Securing Your Site From Further Attack
Afterwards, I went to all of my customer WordPress sites and implemented a series of security measures to combat these types of attacks. I didn’t want to see a repeat of this ordeal, ever.
Here’s what I did:
- Changed all passwords to something complicated. I use the site passwordgenerator.net to create complex passwords. WEAK PASSWORDS ARE THE WEAKEST LINK IN THE SECURITY CHAIN. If you have a lousy password, change it immediately.
- Many websites can be accessed through cpanel by typing [domain-name].com/cpanel into your browser. Make sure to harden up the login and password for cpanel also.
- Added either the Sucuri or iThemes security plugins, and sometimes both of them.
- Used the hardening features of the above plugins to harden against hacker attacks.
- Ran the free Sucuri Sitecheck to check for malware.
- Turned on the Protect feature of Jetpack, which protects against brute force attacks.
- If the customer didn’t have Jetpack for some reason, I added the BruteProtect plugin, which is free and does the same thing.
- Added the Math Captcha plugin to further secure the login page.
- Upgraded to the latest version of WordPress, which at the time of this article is 4.2.2.
- Upgraded all plugins and deleted any extraneous ones.
- Deleted extraneous themes. I prefer to have exactly one theme in my themes directory.
- Upgraded the active theme if an upgrade was available.
- In several cases I deleted the “admin” user.
- Deleted users with simple usernames (e.g. “bob”) and created complicated usernames. See below for why…
100% of WordPress Sites Are Subjected To Hacker Attacks
Here’s the really scary part. After securing all of my customer sites and monitoring their logs for a couple of weeks, I found that 15 out of my 15 WordPress sites were hit with brute force attacks regularly. Some were hit every single day. Some were getting hit while I was logged in and working on them.
It’s my strong belief that all WordPress websites are subjected to hacker attacks. 100%. That was shocking to me, and it made me realize that security is a gigantic issue that most site owners don’t think about enough.
Even if the number of WordPress sites targeted by hackers isn’t actually 100%, we should be treating it like it is. You simply don’t want to take the chance, especially when all of the tools for heightened security are out there and free.
One other note. If you run a blog with multiple authors and the author names are shown on the posts, the hacker bots can scrape those names and use them for brute force attempts. Thus, if you have an author name of “Bob” on your homepage, expect to see illegal login attempts from Bob. Make sure your usernames and display names are different. For better security, make usernames complicated and unguessable.
Why is it so easy for hackers to target sites on the regular? Hackers use bots, and they can configure the bot to accumulate huge lists of websites that have potential security holes (e.g. WordPress sites) and then set the bot to do regular brute force attempts. It’s all automatic.
What Else? — Try Clef
I’ve installed the Clef plugin on several of my blogs and I love the way it works. Essentially, it uses a smartphone app to sync with a waveform on the login page instead of using login names and passwords. You read that right, a waveform. It’s some cool sci-fi stuff. Because of the two-factor authentication process, it’s virtually impossible for a brute force attack to gain entry to your site.
The only drawback I see with Clef is if you have a bunch of users and not all of them are savvy enough to set up the Clef app on their phones or maybe a user just doesn’t have a smartphone. It’s possible. But I think Clef is perfect in situations where the webmasters are the only people accessing a site.
Plus, Clef is kind of fun to use:
My final advice: secure your website immediately. You can do all the steps I outlined above in less than an hour. If you’re having problems or need help dehacking a WordPress site, feel free to contact me.