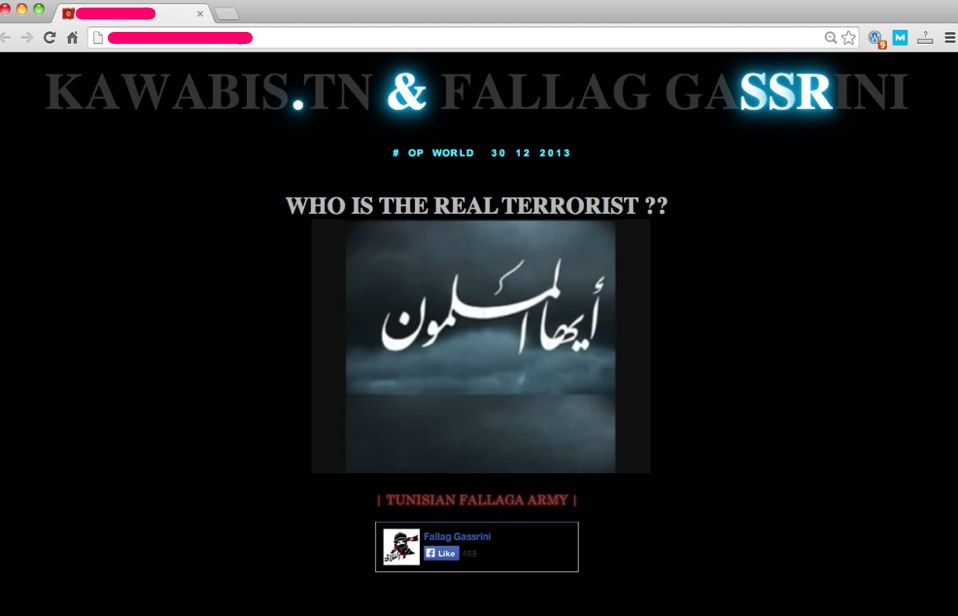
I manage and provide services for a number of WordPress site owners and recently one of client sites was hacked. When you surfed into the site URL, you were greeted with a defacement page that looked like this:
It included music, an animated GIF, and even a Facebook like button for the hacker! Understandably, my clients were shocked when they discovered it and so were several of their regular readers. We still had access to the site admin and other pages on the site, so I quickly logged in and did an assessment.
I deleted all user profiles and re-created an admin profile for my client with a stronger password. I also changed the secret keys in the wp-config.php file to invalidate any session cookies in case the hacker had those stored on his system. You can generate random secret keys on this page at WordPress.org:
https://api.wordpress.org/secret-key/1.1/
If your site’s been hacked, the best place to start reading is FAQ My site was hacked at WordPress.org. There are links to several excellent articles and resources that gave me a pretty thorough strategy for de-hacking and cleaning my client site. I paid close attention to his article: How To Completely Clean Your Hacked WordPress Installation.
Notably, I found two suspicious files in the theme directory: index.php and 404.php. I eyeballed all of the theme file sizes via FTP and saw both files were enormous, so I removed them immediately. I checked all other theme files, spot checked several WordPress files (wp-config.phg and .htaccess chief among them), and checked several blog posts to see if any weird javascripts or malware was embedded. I didn’t find anything additional.
Here’s a screenshot of index.php code the hacker left as the defacement page if you’re interested in this sort of thing:
 My next step was to completely replace WordPress with a fresh download (v3.8) and reload the wp-content folder from a backup I had of the site. I have my clients on regular site backup plans, so this came in very handy.
My next step was to completely replace WordPress with a fresh download (v3.8) and reload the wp-content folder from a backup I had of the site. I have my clients on regular site backup plans, so this came in very handy.
After I spent a few hours cleaning and testing, I ran the site through SiteCheck by Sucuri, an awesome free resource for testing your site for malwares and other unhealthy parasites. If you’re a site owner, I highly recommend running all of your sites through the tool. My client site received a clean bill of health. What’s nice about SiteCheck is it locates all of the javascripts and iframes and tells you exactly where they are located, which is a common starting point for malwares.
One more tip, I used the Bulletproof Security plugin to quickly see if there were any security holes on the site and plug them if necessary.
I did a bunch of Google searches on “Fallaga Tunisian Army” and “Fallag Gassrini” to see if there was a specific de-hacking strategy posted and couldn’t find anything, but there are multiple hacked sites attributed to Fallag and his hacker group. You can read an article about it at hackread.com. If you poke around, you can even see other hacked sites with similar defacement pages online.
If anyone has other specific tactics for combatting this particular hack, please let me know!
Takeaways: Always keep your WordPress install and plugins up-to-date, remove any unused plugins and themes, and make sure you have super strong passwords. Make regular backups and monitor everything closely.